He holds a Master’s of Science degree in Information Technology with a specialization in Information Assurance, a Master’s of Arts and Religion in Pastoral Counseling, and a Bachelor’s of Science in Human Resources Management. He lives in the greater Washington D.C./Baltimore, Maryland
1. Anatomy of a Cyber Attack - Beginner Hacking with Metasploit
Learn the attacker's methodology and start your career in cybersecurity, penetration testing, and ethical hacking!
Start now Anatomy of a Cyber Attack - Beginner Hacking with MetasploitAnatomy of Advanced Persistent Threats
If you know how they work, you can learn how to stop them
From cyber criminals who seek personal financial information and intellectual property to state-sponsored cyber attacks designed to steal data and compromise infrastructure, today’s advanced persistent threats (APTs) can sidestep cyber security efforts and cause serious damage to your organization. A skilled and determined cyber criminal can use multiple vectors and entry points to navigate around defenses, breach your network in minutes and evade detection for months. APTs present a challenge for organizational cyber security efforts.
The six steps of an APT attack
To improve your cyber security and successfully prevent, detect, and resolve advanced persistent threats, you need to understand how APTs work:
The cyber criminal, or threat actor, gains entry through an email, network, file, or application vulnerability and inserts malware into an organization's network. The network is considered compromised, but not breached.
The advanced malware probes for additional network access and vulnerabilities or communicates with command-and-control (CnC) servers to receive additional instructions and/or malicious code.
The malware typically establishes additional points of compromise to ensure that the cyber attack can continue if one point is closed.
Once a threat actor determines that they have established reliable network access, they gather target data, such as account names and passwords. Even though passwords are often encrypted, encryption can be cracked. Once that happens, the threat actor can identify and access data.
The malware collects data on a staging server, then exfiltrates the data off the network and under the full control of the threat actor. At this point, the network is considered breached.
Evidence of the APT attack is removed, but the network remains compromised. The cyber criminal can return at any time to continue the data breach.
Traditional cyber security measures such as defense-in-depth, firewalls and antivirus cannot protect against an APT attack, and leave organizations vulnerable to data breaches. The Adaptive Defense approach from FireEye is the best strategy to intercept possible APTs at any point in your network, analyze them with the latest available information on threat actors and methodology, and support your security professionals with extensive knowledge of industry and threat groups they may encounter.
Introduction
Security is everyone’s job today, from consumers, to system administrators, to executives. If you are doing
business, you need to elevate the priority of security across your organization and data center. Over the years,
cybercriminals have gotten more advanced and better funded. They are entire teams of highly trained hackers, and
they have built it into a very profitable business. Cybercrime is big business. In many cases, states have built their
own cyberattack teams. These teams are no less important to their state strategies than their army or navy. And just
like these cyber-attack teams are prepared to attack anyone, you too must be prepared to defend against anyone.
Whether you know it or not, you are in a cyber war.
You need to be prepared.
THE ANATOMY OF A CYBER ATTACK: DISSECTING THE SCIENCE BEHIND VIRTUAL CRIME
The Anatomy of a Cyber Attack
Reconnaissance
The first part of the anatomy of a cyber attack is reconnaissance. Hackers usually start by researching and gathering information about the target organization. They look for network ranges, IP addresses, and domain names. And, hackers also search for email addresses of key players in the organization such as CFOs, IT professionals, and CTOs. If the hackers fail to find the email addresses of key players, then they identify vulnerable employees by sending phishing emails. Next, the attackers scan for vulnerabilities in the network, which is a long process, that sometimes, take months. After they get an entry to the organization via network vulnerabilities or employee email address, attackers proceed to the next phase.
Attack
After getting access to the network, a hacker proceeds to infiltrate the organization’s network. But, to access the network freely, the attacker needs access privileges. Hence, attackers use rainbow tables and similar tools, which help them in stealing credentials to upgrade their access to administrator privileges. Now, hackers can access the entire network, and go through the network silently. Then, attackers are free to obtain sensitive information for selling on the internet or encrypt the data to demand ransom. Sometimes, hackers may also alter or erase sensitive data for reasons beyond financial gain.
Expansion
The next phase of the anatomy of a cyber attack is expansion. Hackers intrude all systems on the network using malicious programs. Malicious programs enable attackers to hide in multiple systems in the organizations and regain access to the network even after being detected. Additionally, hackers no longer require higher access to infiltrate the network.
Obfuscation
Hackers proceed to hide their tracks to mask the origins of the attack. Additionally, the attackers safely place their exploit in a system to avoid getting detected. The main purpose of obfuscation is confusing and disorienting the forensic experts. For successful obfuscation, hackers use various tools and techniques such as spoofing, log cleaning, zombied accounts, and Trojan commands. Cybersecurity experts generally consider obfuscation as the final stage of the anatomy of a cyber attack.
Understanding the Motive behind Cyber Attacks
To effectively protect your organization from cyber attacks, it is essential to understand the motive behind cyber attacks. The motives of a hacker can help find flaws in the anatomy of a cyber attack. For example, the WannaCry ransomware was recently used to attack several hospitals and GP clinics all over the United Kingdom, which cost the NHS almost £92m. The attackers exploited a leaked NSA tool to attack vulnerable Windows systems and encrypt sensitive information. Furthermore, the attack canceled over 19,000 appointments. Similarly, ransomware is used by attackers to encrypt vital information and extort ransom in exchange for decrypting data. Another reason could be cyber terrorism to create fear among the masses. Alternatively, major cyber attacks can also serve as a distraction for something darker behind the curtains.
Preventing the Organization from Cyber Attacks
To protect the organization, business leaders such as CIOs and CTOs need to hire skilled cybersecurity professionals. Cybersecurity experts spend years in researching and studying the anatomy of a cyber attack, and they know how to prevent or at least minimize the impact of cyber attacks. Cybersecurity experts can maintain the security standards in your organization through multiple steps and measures such as follows:
Cybersecurity experts test the systems and the network for vulnerabilities and fix them preemptively.
Intrusion prevention technology is capable of detecting reconnaissance attempts. And, URL filtering and reputation-based security services can block suspicious links that may contain viruses or malware.
Cybersecurity experts install firewalls and malware scanners to block malware and viruses. Malware is constantly redesigned by attackers to avoid being detected by traditional signature-based systems. Hence, advanced persistent threat protection needs to be used to detect malware based on malware behavior.
Organizations need to pay close attention to the outgoing traffic and apply egress filter to monitor and restrict outgoing traffic.
Cybersecurity experts must conduct regular audits of hardware and software to monitor the health and security strength of their IT systems.
Organizations should consider training employees and educating them about cyber attacks as one of their top priorities.
Creating Damage Reduction and Recovery Strategies
Organizations have to realize that even after following all the security protocols, hackers can still attack their networks and systems. With the help of cybersecurity experts, organizations can analyze the anatomy of a cyber attack to find flaws in the attacks, and exploit the weaknesses to reduce the damage. Various organizations only plan for protection from cyber threats, completely avoiding recovery mechanisms, which can lead to dire consequences in case of an attack. For example, Google is shutting down Google+ due to a data breach that compromised 500,000 user accounts in 2015. But, Google announced that they became aware of the breach during March and June 2018. Learning from the example of Google, organizations should know the importance of minimizing the damage. To reduce the damage from cyber attacks, organizations should consider the following steps:
The first step would be encrypting all the data that your organization owns. Even if an attacker infiltrates the network, decrypting the data will need hours, which may buy some time for the security experts to find the source of the attack.
Organizations must adopt two-factor authentication system, as passwords can get leaked easily. With two-factor authentication, the attacker cannot access the data even after acquiring the leaked passwords.
For better data loss prevention, cybersecurity systems should set up alerts for outgoing data. The alerts can notify the organization about their data being stolen after a data breach.
Hackers control the systems and networks with malware-based communication systems. Hence, blocking outgoing command and control connections can effectively stop outgoing malware communication.
Applying Modern Technologies for Better Cybersecurity
Artificial intelligence is playing a pivotal role in cybersecurity. Machine learning has the ability to analyze the anatomy of a cyber attack, and learn from the behavior patterns of malware. Moreover, artificial intelligence can automate threat detection and data recovery mechanisms. Hence, AI-powered applications can find security threats and implement recovery strategies more efficiently when compared to software-based solutions. And, big players such as Microsoft, Google, Palo Alto Networks, Fortinet and Cisco Systems are already developing cybersecurity solutions using artificial intelligence and machine learning. With the exponential development of artificial intelligence, numerous security software have started adopting machine learning to provide more effective cybersecurity solutions.
Likewise, blockchain technology has the potential to improve cybersecurity. Blockchain can effectively detect a data breach, and disrupt the process that forms the anatomy of a cyber attack. With blockchain, organizations can distribute their data over the network, which will simplify the process of data recovery. And, the changes in data would be transparent. Hence, if the data is altered or deleted, tracking the changes will be an easy process. Furthermore, multiple cybersecurity firms are working on developing blockchain-powered security solutions for mainstream applications. For example, Acronis, a cybersecurity organization, is applying blockchain technology to generate a cryptographic hash, that is unique for every data file. The hash can be used to verify the authenticity of every file. And, it is almost impossible for a hacker to compute the cryptographic hash. Thus, AI and blockchain are revolutionizing the cybersecurity landscape.
Although the technology and methods to fight cyber attacks are getting better, hackers are also developing their techniques to execute stronger attacks. And, with new malware and ransomware being developed, these attacks can lead to bigger data breaches than any we’ve seen before. Hence, organizations need to become aware of the anatomy of a cyber attack to be able to tackle cybersecurity issues better.
7 Phases of a Cyber Criminal’s Methodology.
Hacks are ever-evolving and come in all shapes and sizes, making it dangerous to muddle them together into one category. But having said that, outlining the general methodology of most cyber-attacks in seven phases can be helpful for mapping tactical threat intelligence.
Inspired by Lockheed Martin’s Cyber Kill Chain, we associated each phase of a cyber-attack with the anatomy of a bug (pun intended). Much like a living creature, the state of each organ or limb affects the health of the entire organism. The more victims know about each stage, the better they can prevent and respond to attacks – so that critical assets don’t end up in the criminal’s belly every time.
Here are 7 components in the anatomy of a cyber-attack, each explained by Fortinet:
1-Reconnaissance: Attacker needs to understand as much as they can about an organisation and its network to plan their attack. So at this stage, an organisation’s defence and response mechanisms are researched and tested. Attackers looking for unpatched devices or operating systems use social media to learn about employees and look for other important company information, such as what applications it might have on its network. They may also research the victim’s business partners to assess if one of them has a weaker security stance that can become a pathway into the desired network.
2 -Weaponisation: Once vulnerabilities are identified within the targeted organisation, attackers build malicious code to exploit them undetected. If the attacker is a nation state actor they are likely to use a zero-day exploit, but most cyber criminals use exploit kits focused on publicly known vulnerabilities. Many of such kits use evasion techniques that can by-pass a number of technological controls, such as firewalls and antivirus.
3 -Delivery: Once the cyber-weapon is chosen and/or built, the attacker needs to find the best mechanism to deliver it. Delivery vehicles include infected websites, malvertising, and one of the most common: phishing emails and social engineering. With so much information online about employees, phishing emails are becoming extremely personalised and increasingly harder to distinguish from a legitimate one. Unfortunately, all the threat actor needs in order to succeed on this stage is to trick one employee into clicking a link.
4 – Exploitation: Once the exploit is delivered, it needs to be executed without being detected. With phishing emails as a preferred tool, many attacks are performed in the client-side of the network, focused on the user’s browser and its vulnerable plug-ins, such as flash and java. Other exploits deliver malicious macros and scripts hidden inside documents sent to other users.
5 – Command & Control: Once successfully executed, the exploit tries to communicate with the threat actor behind it in order to download malware and other tools to further compromise the invaded network. In order to communicate undetected, commands and requests are usually tunnelled through protocols such as HTTP(S), DNS, or TOR and communications is often encrypted.
6 – Internal reconnaissance: Since the first insertion point is usually a vulnerable workstation, attackers need to move laterally through the victim’s network in order to map its infrastructure and find the data they are looking for to complete their cyber mission. To do that, they need to compromise other devices, including IoT and healthcare devices in the network. A good place to start is finding a server that stores all user and device credentials, such as an Active Directory Server.
7 -Maintain: Attackers want to stay for as long as possible in the victim’s network, so they dig deep inside it to maintain a foothold -by installing things such as rootkits for hiding files, or kernel-mode rootkits called bootkits. Bootkits can infect start-up code in order to gain unrestricted access to an entire computer, so the exploit can control all that the user is allowed to see. But it can become challenging for the attacker when the data they want to steal is not located on a device with direct access to the internet. In this case, once the threat actor has targeted the data, they may need to find and compromise another server that has access to the Internet to be used as a staging area – an intermediate storage area that allows for the extraction process –, such as data warehouses or other data repositories.
Description
Updated with the EternalBlue & WannaCry Ransomware Exploit Labs against Windows 7/Server 2008 victims!** Dissect the Threat! Understand the Importance of Cyber Security **
- anatomy of an attack
- list of apts cyber
- list of cyber terrorism attacks
- advanced persistent threat attack
- advanced persistent threats cybersecurity
- apt cyber
- fireeye apt
- apt cyber security
Your networks are facing a constant barrage of attacks by malicious actors: hackers, hacktivists, script kiddies, advanced persistent threats, and even nation states are all searching for footholds into networks around the globe. System administrators have always been the first line of defense in system security, and in this global cyber war your role has become increasingly important to the security our networks. As the lynchpin to network defense, it is imperative that system administrators understand the vulnerabilities and methodology employed by malicious cyber actors in order to assist in stopping cyber attacks.
In “The Anatomy of a Cyber Attack”, you will learn to dissect the techniques used by hackers in their exploitation of a network. From open-source research and reconnaissance to the exploitation and covering of their tracks, you will learn hands-on techniques to probe your network for vulnerabilities and understand how they are exploited. Taught by an expert in cybersecurity, you will learn to think like a hacker in order to thwart their future attacks on your networks.
A truly eye-opening experience into the world of cybersecurity, “The Anatomy of a Cyber Attack” is essential to understanding the landscape of today’s cyber threats.
What You Will Receive In The Course:
Video lectures that are fun, entertaining, and enlightening
Walkthrough of building your own penetration testing lab for use in the course
Labs for every step of the hacker methodology
You can watch the instructor to better understand the threat, or learn to conduct the attack yourself using Metasploit!
Practice questions to ensure mastery of each section of the course
A solid foundation upon which to conduct further study or certification preparation
This course provides a great foundation upon which to build upon for Certified Ethical Hacker (CEH) or penetration testing studies!
What This Course Is NOT:
Certified Ethical Hacker preparation course
IT Certification preparation course
Designed to provide a mastery of penetration testing techniques (but will give you a great introduction)
What Students Are Saying About This Course:
This is impressive, opened my eyes, and taught me skills necessary for my career. Thanks, Jason! Really good work! (Wayne, 5 stars)
One of the best courses I have seen to integrate lecture with demo/labs. (Greg, 5 stars)
Nice overview with practical examples. You get an introduction to the tools used so that can be used as a starting point to learn more. (Seppo, 5 stars)
This course is designed for all IT personnel and provides a great overview of the need for cybersecurity through hands-on examples of network and system exploitation. Even beginners will be able to understand the concepts and enjoy the course, but may have some difficult in conducting the attacks themselves. A basic understanding of computers and computer networks is required to understand this course.
Who this course is for:
Students who are interested in the cyber threat that exists in today's culture
Students interested in learning how hackers are able to attack networks and information systems
Students looking for a beginner/overview course for penetration testing and hacking
Students wanting an easy to understand course on using Metasploit to conduct penetration testing
What you'll learn
Understand the steps of a cyber attack
Understand the basic methodology, tools, and techniques used by hackers in exploiting networks and information systems
Requirements
PC or Mac with at least 4 GB of RAM in order to install the virtualization software used in this course
Windows XP disc or disc image to setup a vulnerable machine for the labs
Kali Linux disc image (free to download, instructions provided in the course)
VirtualBox software (free to download, instructions provided in the course)
2. WiFi Hacking - Wireless Penetration Testing for Beginners
Complete guide to hacking WiFi (WEP, WPA, & WPA2) wireless security and how to exploit (pentest) their vulnerabilities!
Start now WiFi Hacking - Wireless Penetration Testing for Beginnershackers come in all shapes, sizes and colors. Hacking is a very wide term. And by the first sentence, I'm not referring to the physical characters of the hackers, I'm talking about the field of specialization. Believe me, there is a lot of work to do on the Wireless domain that we had been working on so far (we have only touched wireless networks for the time being - you are a beginner), but wireless hacking is but a small island in the vast sea of hacking. A relatively large landmass is unarguably Penetration Testing, and a large name in this context is Metasploit. So here's a guide which will give you a good idea about what Penetration testing is, and if you're feeling to lazy, I've got it summarized here.
What is a penetration test?
What is penetration testing? Penetration testing, often called “pentesting”,“pen testing”, or “security testing”, is the practice of attacking your own or your clients’ IT systems in the same way a hacker would to identify security holes. Of course, you do this without actually harming the network. The person carrying out a penetration test is called a penetration tester or pentester.
How legal is it?
Let’s make one thing crystal clear: Penetration testing requires that you get permission from the person who owns the system. Otherwise, you would be hacking the system, which is illegal in most countries – and trust me, you don’t look good in an orange jump suit (or maybe you do, still I don't recommend going to jail for it, buy one if you need it).
In other words: The difference between penetration testing and hacking is whether you have the system owner’s permission. If you want to do a penetration test on someone else's system, it is highly recommended that you get written permission. Much better, get your virtual machine up and running, with your already acquired VMWare skills, and practice on your own system.
What is a vulnerability?
A vulnerability is a security hole in a piece of software, hardware or operating system that provides a potential angle to attack the system. A vulnerability can be as simple as weak passwords or as complex as buffer overflows or SQL injection vulnerabilities. (SQL injection is another topic I'd like to touch. Later maybe. I'm taking up too many tasks at hand at once.)
What is security research?
Vulnerabilities are typically found by security researchers, which is a geeky term for smart people (how much we hackers love to call our self smart, especially the beginners who get too cocky) who like to find flaws in systems and break them.
What is an exploit?
To take advantage of a vulnerability, you often need an exploit, a small and highly specialized computer program whose only reason of being is to take advantage of a specific vulnerability and to provide access to a computer system. Exploits often deliver a payload to the target system to grant the attacker access to the system.
The Metasploit Project host the world’s largest public database of quality-assured exploits. Have a look at their exploit database – it’s right here on the site mentioned in the beginning of the article.
What is a payload?
A payload is the piece of software that lets you control a computer system after it’s been exploited. The payload is typically attached to and delivered by the exploit. Just imagine an exploit that carries the payload in its backpack when it breaks into the system and then leaves the backpack there. Yes, it’s a corny description, but you get the picture.
Metasploit’s most popular payload is called Meterpreter, which enables you to do all sorts of funky stuff on the target system. For example, you can upload and download files from the system, take screenshots, and collect password hashes. You can even take over the screen, mouse, and keyboard to fully control the computer. If you’re feeling particularly bad-ass, you can even turn on a laptop’s webcam and be a fly on the wall.
I would say that a payload is what exploits the 'exploit' and gives you some control over the exploited victim. Meterpreter is THE exploit, cause it doesn't give you 'some' control, it gives you ALL of it (that's some way to put it, yes,but not completely true. It still is the best payload. Beginners/noobs really enjoy the GUI feature available in this payload)
What to do next
Wait for more tutorials, or go ahead learning stuff without me. Not recommended, its gonna be a bumpy ride if you don't have us(I am only one person, why do I keep referring to myself as us?) to stabilize you. But still if you wanna go ahead, then Rapid7 is the best place to get started. Best of luck beginners.
Here is a list of related posts on this blog. You should most probably go in this order.
Penetration Testing Level 1: Hacking Windows XP (actual hacking here after the theory you read in this post- we'll help you setup a Kali Linux attack machine and Windows XP victim machine on VMware. Then wel will perform our first hack)
Penetration Testing Level 2:Post-exploitation of Windows XP
Penetration Testing Level 3:Crashing Windows 7
Armitage : Fast And Easy Hacking GUI
Windows XP : Hollywood Style Hack
Description
This course includes an overview of the various types of wireless (802.11) networks, available encryption security systems (WEP, WPA, and WPA2), and how to use open-source tools to hack and crack these vulnerable wireless (WiFi) networks.Since their introduction in 1999, wireless networks have been rapidly expanding in their usage and availability. Unfortunately, many people believe these wireless networks are designed as a secure solution for sharing data, but this is rarely the case. In this course, you will gain a deeper understanding of the WEP, WPA, and WPA2 wireless security protocols, and how to exploit their vulnerabilities in order to gain access to any wireless network during a penetration test. You will use this information to increase the security of your networks and to implement a better defensive security posture to prevent an attacker from accessing your networks.
What Other Students Are Saying About This Course:
Just completed the course as a newbie and followed all steps exactly and was able to complete everything!! Thank you Jason!!!! (Stephanie, 5 stars)
Great course that goes into detail of how vulnerable Wireless really is... would definitely recommend to anyone who wants to go into InfoSec or Network Security. (Matthew, 5 stars)
Great course. Step by step instructions, good quality audio and video lectures. Easy to understand instructor is very important, especially when he explains everything in detail. (Alisher, 5 stars)
Who this course is for:
Anyone who is interested in understanding the vulnerabilities in wireless security standards such as WEP, WPA, and WPA2
Anyone who wants to learn how to conduct wireless network hacking as part of a penetration test
What you'll learn
How to conduct basic penetration testing on Wireless Networks
How to determine the secret password used by WEP, WPA, and WPA2 networks
How to change your MAC address and impersonate other devices on a wireless network
How to use the Aircrack-Ng tool kit
Requirements
Understanding of the hacker's methodology
Working knowledge of using Kali Linux
Understanding of how computer networking works
3. CompTIA Network+ (N10-007) Full Course & Practice Exam
CompTIA Network+ (N10-007) Bootcamp - Certification preparation course on the most popular networking certification!
Start now CompTIA Network+ (N10-007) Full Course & Practice ExamDescription
** Pass the CompTIA Network+ (N10-007) Exam with Help from an Expert in the Field! **Taught by an expert in information technology and cybersecurity with over 20 years of experience, this course is a fun way to master the fundamentals of networking. I have taught hundreds of students in my bootcamps and college classes on how to pass the A+, Network+, Security+, and Certified Ethical Hacker exams. MY students have achieved a 99% passing rate on their exams, and now you can too!
This course is designed to help prepare you for the CompTIA Network+ (N10-007) certification exam and covers the five domains for the Network+ (N10-007) certification exam: Network Architecture, Network Operations, Network Security, Network Troubleshooting, and Industry Standards, Practices, and Network Theory. You will learn the fundamentals of network and gain experience in the configuration, management, and troubleshooting of common wired and wireless network devices. Also, we will discuss emerging technologies such as unified communications, mobile, cloud, and virtualization technologies.
What You Will Receive In The Course:
Over 8.5 hours of video lectures with the essential information needed to pass the Network+ (N10-007) exam
Downloadable copies of our Network+ (N10-007) Study Notes for the course
Practice questions to ensure mastery of each section of the course
Full-length practice exam to test your knowledge
What Other Students Are Saying About This Course:
I'm using several resources to prepare for the Network+ certification. Jason Dion's "bootcamp" is the best resource I've found, yet! (Kb1vns, 5 stars)
Really enjoyed this course. It kept me engaged and wanting to watch more... would definitely refer this to anyone that is studying for the Network+!. (Rafael, 5 stars)
Very easy to understand explanations, that is very cool! (Vladmir, 5 stars)
Who this course is for:
Students wanting to pass the CompTIA Network+ certification examStudents wanting to learn the terminology and nomenclature of computer networks
Students seeking a career as a network technician
What you'll learn
Passing the Network+ certification exam with confidenceUnderstanding computer networks, their functions, and their components
Subnetting networks
Performing basic network configurations
Becoming an effective networking technician in a small-to-medium sized business environment
Requirements
Basic familiarity with computer networks is helpful (But, all required information will be covered during the course)(Helpful, but not required) Completion of the CompTIA A+ certification
4. ITIL Foundation (2011/v3) Practice Exams (6 Exams)
6 Full-length ITIL Foundation (2011) Exams *** 40 Questions Each & 240 Questions Total (With feedback on each question)
Start now ITIL Foundation (2011/v3) Practice Exams (6 Exams)Description
ITIL® Foundation Sample Questions and Answers– Exam style Test
You are in the best place to practice before taking ITIL-Foundation exam. These questions are in the same style that is used in the exam.
Please note that this is not an official ITIL website and it is built only for you to get yourself familiar with the questions at the exam.
If you study all of the questions in here you will have a good idea about the exams questions styles.
** This course is for the ITIL Foundation (2011 Objectives). If you plan to take the new ITIL 4 Foundation exam, please signup for my brand new ITIL 4 Foundation course instead. **
** Dion Training Solutions is an Accredited Training Organization (ATO) for ITIL® Foundation **
Do you need to earn your ITIL Foundation certification? If so, you've come to the right place!
I have personally trained over 20,000 people in how to pass their ITIL Foundation exam on the first attempt!
With 6 practice exams containing 40 questions each, I have carefully hand-crafted each question to put you to the test. After passing these exams, you will be fully prepared for what it is like to take the Information Technology Infrastructure Library (ITIL) Foundation Certification Exam.
This course is designed around the official Exam Guide from ITIL, weighting the 10 Knowledge Areas appropriately, so you can pass the actual ITIL Foundation Certification Exam with confidence!
You won't be hoping you are ready, you will know you are ready to pass the exam, saving you time and money. After practicing these tests and scoring an 85% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-scheduling fees.
After each practice exam attempt, you will receive your total final score, along with feedback on each and every question -- telling you exactly why each answer is correct so that you can pinpoint the areas in which you need to improve and perform some additional studying.
These ITIL® Foundation Practice Exams have the timed test taking capability and provides you with interactive, question-level feedback.
I have the best-selling ITIL Foundation training course on the Udemy platform and I invite you to visit my instructor profile to learn more about me, the certifications that I hold, and read the reviews of my courses. You won't be disappointed.
This course is constantly updated to ensure it stays current and up-to-date with the latest release of the ITIL Foundation exams, and also provide a 30-day money-back guarantee, no questions asked!
What Other Students Are Saying About This Course:
Very effective tool for preparing to take the ITIL Foundation exam! (Evon, 5 stars)Thank you for the practice exams! Passed on the first try. Thanks again!!!!!! (Desmond, 5 stars)
These exams give the student a very good idea about how difficult the real exam questions will be. I was prepared, and passed the ITIL Foundation Exam this morning. Well worth the cost. (Steve, 5 stars)
The ITIL® course on this page is offered by Dion Training Solutions, LLC, an ATO of AXELOS Limited. ITIL, ITIL Foundation, and the Swirl logo are registered trademarks of AXELOS Limited. All rights reserved.
Who this course is for:
Students preparing for the ITIL Foundation (2011/v3) certification examIT Service Management professionals looking to validate their skills by passing the ITIL Foundation certification
Requirements
Basic understanding of IT Service Management and/or how a service desk works5. CompTIA Network+ (N10-007) 6 Practice Exams and Simulations
Full-length CompTIA Network+ (N10-007) * Timed * 450 Multiple-choice Questions with detailed feedback for each question
Start now CompTIA Network+ (N10-007) 6 Practice Exams and SimulationsDescription
All questions are based on the Exam Objectives for the N10-007 exam for all 5 domains of the exam, so you can take and pass the actual CompTIA Network+ Certification Exam with confidence!In this course, I fully prepare you for what it is like to take the CompTIA Network+ (N10-007) Certification Exam. With 6 full-length practice exams, each of which is timed at 90 minutes, I have carefully hand-crafted each question to put you to the test and prepare you to pass the exam with confidence. Each exam contains practice simulation questions of the Network+ Performance-Based Questions (PBQs), too, because I want to ensure you are ready for the hands-on questions come test day!
After taking these Network+ (N10-007) Practice Exams you won't be hoping you are ready, you will know you are ready to sit for and pass the exam. After practicing these tests and scoring an 85% or higher on them, you will be ready to PASS the Network+ on the first attempt and avoid costly re-schedule fees, saving you time and money.
You will receive your total final score, along with feedback on each and every question, telling you exactly why each answer is correct, so you can pinpoint the areas in which you need to improve and perform some additional study.
These CompTIA Network+ (N10-007) Practice Exams provide you with realistic test questions and provide you with interactive, question-level feedback.
I have one of the best-selling CompTIA Network+ (N10-007) training courses on the Udemy platform and I invite you to visit my instructor profile to learn more about me, the certifications that I hold, and read the reviews of my courses. This course is constantly updated to ensure it stays current and up-to-date with the latest release of the CompTIA Network+ exam, and also provides a 30-day money-back guarantee, no questions asked!
What others are saying about this course:
Just passed Network+. Challenging practice tests help prepare me for the exam. I like the use all resources approach. Now onto Security+!!! (Dan, 5 star)
This set of questions focused me on the required learning and was instrumental in my passing...well worth the cost... (Pranav, 5 stars)
Setup of the questions feels so like being in a real exam environment... loved it! (Behaviour, 5 stars)
Who this course is for:
Students preparing for the CompTIA Network+ (N10-007) Certification ExamRequirements
Basic understanding of networks and network securityHave read a book, watched a video series, or otherwise started studying for the Network+ exam
6. Passing Certification Exams with Strategic Test Taking!
Study smarter and pass your ITIL 4 Foundation, A+, Network+, Security+, PenTest+, CISSP, or other exams easier!
Start now Passing Certification Exams with Strategic Test Taking!Description
This course is designed to help you learn "how to study" for certification exams and understand how to pick the right answers on test day. Now, I know that sounds simple, but there is a method to this that many students don't know...Have you ever taken an IT Certification exam and scored only 695 but needed 700 to pass? Have you had to retake the exam several times in order for you to pass? If so, you may need some help learning how to take certification exams more effectively, because they are different than the tests you took during High School, college, or university.
In this course, you will learn how to study better, take more efficient notes, and most importantly, how to increase your odds of passing your CompTIA (A+, Network+, Security+, CySA+, PenTest+, CASP+), Microsoft, ISC2 (CISSP, SSCP), EC-Council (CEH), or other IT Certification exams on the first attempt by using our tips, tricks, and efficiency gains to your advantage.
After teaching all these techniques in the course, we will dive into some practice exam questions (A+, Network+, Security+, PenTest+, ITIL 4 Foundation, and CISSP) and put these principles to use, showing you how they can help you increase your odds of success, so that you can pass your exam on the first attempt!
What my students are saying about this course:
Amazing course. Straight to the point, makes the learning fast and non complex. Easy to apply straight away. (Dan, 5 stars)
I enjoyed the course so much I ran it from beginning to end on one session. It is very clear and easy to understand and the explanations of tackling test questions should prove very useful. I will definitely be using these techniques in my next exam. (Eddie, 5 star)
I am very interested in cutting my time down on my studies but have the important information. Learning style registers very well with me and some of the things spoken in here appears backwards to those I know, but actually syncs to how I do things. (LaRanne, 5 stars)
Who this course is for:
Students who needs to take IT Certification exams for work or career advancementStudents who are not efficient at studying for their certification exams
Students who have failed on previous attempts on their A+, Network+, Security+, CSA+, ITIL, CEH, or CISSP exams
What you'll learn
To pass your certification exams more easilyTo be more confident when taking your certification exams
To focus your study efforts
To become a better note taker
Requiremets
Be ready to change the way you look at test taking!7. CompTIA CySA+ (CS0-001) 5 Practice Certification Exams
Cybersecurity Analyst+ * 5 Practice Exams * Timed * 60 Questions Each * 300 Questions with full explanations & feedback
Start now CompTIA CySA+ (CS0-001) 5 Practice Certification ExamsDescription
These CompTIA CySA+ (CS0-001) Practice Exams provide you with realistic test questions and provide you with interactive, question-level feedback.In this course, I will prepare you for what it is like to take the CompTIA CySA+ (CS0-001) Certification Exam. With 5 full-length practice exams of 60 unique questions, each of which is timed at 60 minutes, I have carefully hand-crafted each question to put you to the test and prepare you to pass the exam with confidence.
All questions are based on the Exam Objectives for the CompTIA CySA+ (CS0-001) exam for all 4 domains of the exam (Threat Management, Vulnerability Management, Cyber Incident Response, and Security Architecture and Toolsets), so you can take and pass the actual CompTIA CySA+ (CS0-001) Certification Exam with confidence!
After taking this CySA+ (CS0-001) Practice Exam course, you won't be hoping you are ready, you will know you are ready to sit for and pass the exam. After practicing these tests and scoring an 85% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-schedule fees, saving you time and money.
You will receive your total final score, along with a detailed explanation and feedback on every question in our database, telling you exactly why each answer is correct, so you can pinpoint the areas in CySA+ which you need to improve and study further.
This course is constantly updated to ensure it stays current and up-to-date with the latest release of the CompTIA CySA+ exam (CS0-001), and also provide a 30-day money-back guarantee if you are not satisfied with the quality of this course for any reason!
What Other Students Are Saying About This Course:
I used this test prep course ON ITS OWN and PASSED. Period. I am now CySA+ certified thanks to Jason....That's what matters. (Jose, 5 stars)
Excellent check on learning. Author has been extremely responsive and attentive when questions or concerns arise. I highly recommend this for anyone looking to verify their knowledge before taking the CySA+ test. (Darrell, 5 stars)
Used a book and this course, passed first take. (Michael, 5 stars)
Who this course is for:
Students preparing for the CompTIA CySA+ (CS0-001) Certification Exam
Requirements
You should have a basic understanding of networks and network security
You should have read a book, watched a video series, or otherwise started studying for the CySA+ exam
8. Introduction to Malware Analysis for Incident Responders
Increase your cyber security capability by learning to perform dynamic and static malware analysis!
Start now Introduction to Malware Analysis for Incident RespondersDescription
Nearly every incident response that occurs in the cyber security field comes back to the initial intrusion vector: Malware. In this course, you will learn about the various types and categories of malware, their symptoms, and how they work. As an incident responder, it is imperative that you understand the symptoms of malware, but more importantly that you are able to understand WHAT that malware is doing, and quickly.In this course, you will learn how to perform the basics of dynamic malware analysis, a tried and true method of understanding what an unknown binary (malware) is doing on an infected system. You will build your own malware analysis virtual lab to create a safe analysis environment using FlareVM, and then we will perform the analysis on a real-world piece of malware to fully understand the concepts covered in this course.
So, if you have ever wondered how to better understand malware, this is the course for you!
Who this course is for:
Anyone who wants to gain an understanding of how malware functionsAnyone who wants to learn the steps and processes involved in Malware Analysis
What you'll learn
You will understand the steps and processes involved in static and dynamic Malware AnalysisYou will be able to perform basic dynamic Malware Analysis
You will understand the various types of malware found in the wild
Requirements
You should have a general knowledge of computers and operating system fundamentalsYou should have a basic exposure to software development process
It is helpful if you have some experience with programming in C, Java, Python, or another modern language, but it is not required
9. CompTIA CySA+ (CS0-001) Complete Course and Practice Exam
Pass the CompTIA Cybersecurity Analyst+ (CS0-001) exam on your 1st attempt, includes CySA+ practice exam!
Start now CompTIA CySA+ (CS0-001) Complete Course and Practice ExamDescription
**The CompTIA CSA+ certification acronym has changed to the CompTIA CySA+ as of January 2018. The exam content and objectives remain the same.**** Taught by a Best Selling IT Certification Instructor **
This course provides everything you need in order to study for the CompTIA Cybersecurity Analyst+ (CySA+) (CS0-001) exam, including downloadable PDFs of every lecture, 12 quizzes to check your knowledge as you progress through the videos, and a full-length practice exam to test your knowledge before test day!
Taught by an expert in information technology and cybersecurity with over 20 years of experience, this course is a fun way to learn what you need to know to pass the CompTIA Cybersecurity Analyst+ (CySA+) (CS0-001) exam or to better prepare yourself to serve on your organization's cyber defense team.
The CompTIA CySA+ (Cybersecurity Analyst+) (CS0-001) certification is a vendor-neutral certification that validates your knowledge and ability to conduct intermediate-level cyber security skills. This certification was released in February 2017 by CompTIA to fill a gap between the entry-level CompTIA Security+ exam (for those with about 1 year in the field) and the advanced-level CompTIA Advanced Security Practitioner (for those with at least 5 years in the field). The CompTIA CySA+ exam is focused on the technical, hands-on details of the cybersecurity field, including not only cyber threats, secure network architecture, and risk management, but also the ability to perform log analysis, configuration assessments, and more.
This CySA+ (CS0-001) course is designed for IT Security analysts, vulnerability analysts, threat intelligence analysts, or anyone who is trying to get a better understanding of the concepts involved in conducting cybersecurity analysis, to include threat management, vulnerability management, cyber incident response, security architecture, and the toolsets associated with these cybersecurity efforts.
To help you practice for the CompTIA CySA+ (CS0-001) exam, this course even comes with a realistic practice exam containing 85 multiple-choice questions spread across the four domains tested by the CompTIA CySA+ (CS0-001) certification exam!
This course provides full coverage of the four domains of the CySA+ exam:
27%: Threat Management
26%: Vulnerability Management
23%: Cyber Incident Response
24%: Security Architecture and Tool Sets
** Each video lecture comes with a downloadable PDF of all the lecture notes **
What Other Students Are Saying About This CompTIA CySA+ (CS0-001): Complete Course:
Jason Dion as always has some of the best courses. This is the third CYSA+ course I bought from different vendors to see which one would help me more and like always this has already caught my attention and kept me focused the entire time. Other courses have to much distracting factors unlike this one. Will always recommend Jason Dion. (Luis, 5 stars)
Great course, very detailed. Passed the exam on the first try. I have recommended this course to everyone I know in the security industry trying to pass the CySA+ exam. (Jose D., 5 stars)
I have really enjoyed and learnt a lot from this course. I used Jason's course to pass the Network + on my first attempt, I am expecting that this course will enable me to pass the CySA+ too. (Leone W., 5 stars)
Who this course is for:
Students preparing for the CompTIA CySA+ (CS0-001) Certification ExamThreat analysts
Vulnerability analysts
Risk management professionals
Entry-level incident response professionals
What you'll learn
Take and pass the CompTIA CySA+ (CS0-001) certification examUnderstand threat management concepts
Understand vulnerability management concepts
Understand how to conduct a cyber incident response
Understand how to setup a strong security architecture for your networks
Know what different types of cybersecurity tools are on the market and which to use in different scenarios
Requirements
Basic understanding of network and network security(Helpful) Understand the concepts covered by the Network+ and Security+ exams
10. Certified Ethical Hacker (CEHv10) Exams #UNOFFICIAL#
4 Practice Certification Exams * 200 Questions with full explanations * UNOFFICIAL CEH (312-50) Exam Practice Questions
Start now Certified Ethical Hacker (CEHv10) Exams #UNOFFICIAL#Description
A Certified Ethical Hacker is a skilled professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). The CEH credential certifies individuals in the specific network security discipline of Ethical Hacking from a vendor-neutral perspective.The Purpose of the CEH credential is to:
Establish and govern minimum standards for credentialing professional information security specialists in ethical hacking measures.
Inform the public that credentialed individuals meet or exceed the minimum standards.
Reinforce ethical hacking as a unique and self-regulating profession.
About the Exam
Number of Questions: 125
Test Duration: 4 Hours
Test Format: Multiple Choice
Test Delivery: ECC EXAM, VUE
Exam Prefix: 312-50 (ECC EXAM), 312-50 (VUE)
Passing Score
In order to maintain the high integrity of our certifications exams, EC-Council Exams are provided in multiple forms (I.e. different question banks). Each form is carefully analyzed through beta testing with an appropriate sample group under the purview of a committee of subject matter experts that ensure that each of our exams not only has academic rigor but also has “real world” applicability. We also have a process to determine the difficulty rating of each question. The individual rating then contributes to an overall “Cut Score” for each exam form. To ensure each form has equal assessment standards, cut scores are set on a “per exam form” basis. Depending on which exam form is challenged, cut scores can range from 60% to 85%.
Certified Ethical Hacker (CEH) is a qualification obtained by demonstrating knowledge of assessing the security of computer systems by looking for weaknesses and vulnerabilities in target systems, using the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system. This knowledge is assessed by answering multiple choice questions regarding various ethical hacking techniques and tools. The code for the C|EH exam is 312-50. This certification has now been made a baseline with a progression to the C|EH (Practical), launched in March 2018, a test of penetration testing skills in a lab environment where the candidate must demonstrate the ability to apply techniques and use penetration testing tools to compromise various simulated systems within a virtual environment.
Ethical hackers are employed by organizations to penetrate networks and computer systems with the purpose of finding and fixing security vulnerabilities. The EC-Council offers another certification, known as Certified Network Defense Architect (CNDA). This certification is designed for United States Government agencies and is available only to members of selected agencies including some private government contractors, primarily in compliance to DOD Directive 8570.01-M.[1] It is also ANSI accredited and is recognized as a GCHQ Certified Training (GCT).
"Certified Ethical Hacker" and "CEH" is a registered trademark of EC-Council and this course is not licensed, endorsed or affiliated with EC-Council in any way.
These UNOFFICIAL Certified Ethical Hacker (CEH 312-50 v10) Practice Exams provide you with realistic test questions and provide you with interactive, question-level feedback. In this course, I will prepare you for what it is will be like to take the Certified Ethical Hacker (CEH) Certification Exam. With 4 practice exams, each of which is timed at 100 minutes, I have carefully hand-crafted each question to put you to the test and prepare you to pass the exam with confidence.
This practice exam course is an UNOFFICIAL course made by an instructor who holds the Certified Ethical Hacker certification to help provide you additional study questions after you have taken an official training from Ec-Council.
These practice exam questions are based on the Exam Objectives for EC-Council's Certified Ethical Hacker (CEH) exam for all areas of the exam (Background, Analysis/Assessment, Security, Tools/Systems/Programs, Procedures/Methodology, Regulation/Policy, and Ethics) to help better prepare you for the real certification exam.
You won't be hoping you are ready, you will know you are ready to sit for and pass the exam. After practicing these tests and scoring an 90% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-take fees, saving you time and money.
You will receive your total final score, along with a detailed explanation and feedback on every question in our database, telling you exactly why each answer is correct, so you can pinpoint the areas in which you need to improve and study further.
This course is frequently updated to ensure it stays current and up-to-date with the latest release of the certification exam, and also provides you with a 30-day money-back guarantee if you are not satisfied with the quality of this course for any reason!
What Other Students Are Saying About This UNOFFICIAL Practice Exam Courses:
Excellent check on learning. Author has been extremely responsive and attentive when questions or concerns arise. I highly recommend this for anyone looking to verify their knowledge before taking the test. (Darrell, 5 stars)
What I like most about his courses are the explanation of why an answer is correct [and] his prompt response to my questions. (Jin, 5 stars)
Used a book and this course, passed first take. (Michael, 5 stars)
Excellent study questions and preparation for the exam. (Christopher, 5 stars)
“Hacker” didn't start out as a bad word, but it's evolved into one, thanks to hackers of the malicious kind. Despite how oxymoronic the term “ethical hacker” may seem, the Certified Ethical Hacker credential is no joke.
Certified Ethical Hacker (CEH) is a computer certification that indicates proficiency in network security, especially in thwarting malicious hacking attacks through pre-emptive countermeasures.
Malicious hacking is a felony in the U.S. and most other countries, but catching criminals requires the same technical skills that hackers possess.
About the CEH
The CEH credential is a vendor-neutral certification for information technology professionals who wish to specialize in stopping and identifying malicious hackers by using the same knowledge and tools the criminals use.Even before the credential was introduced, private firms and government agencies were hiring reformed malicious hackers because they believed that was the best method for securing their networks. The CEH credential takes this a step further by requiring those who earn it to agree in writing to abide by the law and honor a code of ethics.
The credential is sponsored by the International Council of E-Commerce Consultants (EC-Council), a member-supported professional organization. Its goal, according to its website, is to establish and maintain standards and credentials for ethical hacking as a profession and to educate IT professionals and the public on the role and value of such specialists.
In addition to CEH certification, the EC-Council offers several other certifications relevant for network security jobs, as well as those for secure programming, e-business, and computer forensics jobs. Certification proficiency levels range from entry-level to consultant (independent contractor).
How to Become a CEH
Students who have a minimum of two years of security-related job experience can apply for approval to take the EC-Council exam. Those without two years of experience will be required to attend training at an accredited training center, through an approved online program, or at an approved academic institution. These requirements prepare applicants for the exam and help screen out malicious hackers and hobbyists.
As of 2018, the courseware price for the five-day certification course was $850. The application fee for those seeking to bypass the training course was $100, and the exam voucher price was $950.
The Course
The CEH Training Program prepares students to take the CEH 312-50 exam. It consists of 18 modules covering 270 attack technologies and mimics real-life scenarios in 140 labs. The course is run on an intensive five-day schedule with training eight hours per day.
In the end, the goal is for students to be ready for the exam in addition to being ready to handle whatever penetration testing or ethical hacking scenarios come their way in their IT security careers.
The Exam
The 312-50 exam lasts four hours, comprises 125 multiple-choice questions, and tests CEH candidates on the following 18 areas:
Introduction to ethical hacking
Footprinting and reconnaissance
Scanning networks
Enumeration
System hacking
Malware threats
Sniffing
Social engineering
Denial of service
Session hijacking
Hacking web servers
Hacking web applications
SQL injection
Hacking wireless networks
Hacking mobile platforms
Evading IDS, firewalls, and honeypots
Cloud computing
Cryptography
Job Outlook
IT security is a fast-growing field, and the U.S. Bureau of Labor Statistics (BLS) projects job growth at a rate of 28 percent for the decade ending in 2026. This is far greater than job growth of 7 percent projected for all professions combined. The median annual wage for IT security analysts, as of 2017, was about $95,000, according to the BLS.
A quick search on Indeed shows that many security jobs require or recommend a CEH credential, so candidates who possess one will be more marketable.
Most jobs that CEH-credentialed professionals pursue put candidates through background checks or more rigid personnel security investigations (PSIs). Security clearances likely will be required at government agencies or private firms with government contracts.
Success Stories
Many of the high-profile stories about ethical hackers involve the biggest companies in technology. Companies like Apple, Google, and others will challenge ethical hackers to break their security measures in order to help them find weaknesses and to make their products safer. They often offer a lot of money to anyone who can find a weakness.
In 2016, Nimbus Hosting listed some of the more famous success stories of ethical hackers. Among them are examples of a security team offering a reward to anyone who could take over an iPhone or iPad, and an anonymous hacker who went by the name Pinkie Pie who helped identify a bug in Google Chrome. Not all of these examples involve professionals following the CEH-certification route, but they show the value companies place on hiring hackers to help shore up network security.
Who this course is for:
Students preparing for EC-Council's Certified Ethical Hacker (CEH) Certification ExamRequirements
You should have a basic understanding of networks and network securityYou should have read a book, watched a video series, or otherwise started studying for the Certified Ethical Hacker (CEH) exam
11. PRINCE2 Foundation Practice Certification Exams (6 Exams)
6 Full-length PRINCE2 Foundation Practice Tests *** 60 Questions Each & 360 Questions Total (With feedback per question)
Start now PRINCE2 Foundation Practice Certification Exams (6 Exams)Description
** Based on the latest PRINCE2® 2017 Objectives **Have you already taken an PRINCE2 Foundation course from a registered Accredited Training Organization (ATO)?
Have you self-studied using the Managing Successful Projects with PRINCE2 textbook?
Are you still not quite confident that you are ready to take the certification exam? If so, you've come to the right place!
I have personally trained over 5,000 people in how to pass their PRINCE2 Foundation exams on the first attempt!
With my 6 practice exams containing 60 questions each, I have carefully hand-crafted each question to put you to the test. After passing these exams, you will be fully prepared for what it is like to take the PRINCE2 Foundation Certification Exam.
This course is designed around the official Exam Guide from PRINCE2, so you can pass the actual PRINCE2 Foundation Certification Exam with confidence!
You won't be hoping you are ready, you will know you are ready to pass the exam, saving you time and money. After practicing these tests and scoring an 75% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-scheduling fees.
After each practice exam attempt, you will receive your total final score, along with feedback on each and every question -- telling you exactly why each answer is correct so that you can pinpoint the areas in which you need to improve and perform some additional studying.
These PRINCE2® Foundation practice exams have the timed-test taking capability and provides you with interactive, question-level feedback.
These practice exams are constantly updated to ensure it stays current and up-to-date with the latest release of the PRINCE2 Foundation exam, and also provide a 30-day money-back guarantee, no questions asked!
What Other Students Are Saying About My PRINCE2 Foundation Practice Exam Course here on Udemy:
The practice questions are really helpful. I highly recommend to anyone looking for perfect practice exams. (Vamsidhar, 5 stars)
Great practice exams... if you can answer these, you can definitely pass the exam! (Miguel, 5 stars)
Excellent training material. I don't think I would have passed the exam without working on these extra practice exams first. (Anders, 5 stars)
** Dion Training Solutions (diontraining) is an Accredited Training Organization (ATO) for PRINCE2® Foundation certification. These practice exams make an excellent supplement to your other study efforts for the PRINCE2® Foundation certification, but should not be your only resource for studying for this exam. It is recommended that you attend a full training course prior to taking the exam. **
The PRINCE2® course on this page is offered by Dion Training Solutions, LLC, an ATO of AXELOS Limited. PRINCE2 and the Swirl logo are registered trademarks of AXELOS Limited. All rights reserved.
Who this course is for:
Students preparing for the PRINCE2 Foundation certification examProject Management professionals look to validate their skills by passing the PRINCE2 Foundation certification
Requirements
Basic understanding of how Project Management works (either PMP or PRINCE2)Desire to pass the PRINCE2 Foundation certification exam
PRINCE2 Foundation training (Video-based course or textbook) from an Accredited Training Organization
12. Risk Management for Cybersecurity and IT Managers
The management's guide to understanding Risk Management decisions in cybersecurity and information technology (IT)!
Start now Risk Management for Cybersecurity and IT ManagersDescription
Have you ever wondered why your organization's executives or your manager made a decision to fund or not fund your project?
In this course, you will get an inside look at how cybersecurity and information technology (IT) managers determine which projects they will support with funding and which they won't based on a preliminary risk analysis. Over the past two decades, I have worked in the cybersecurity and information technology realm, fighting for my projects to become funded. Early in my career, I didn't understand why certain projects would be funded and executed, while others wouldn't. What I learned, is that it all came down to Risk Management by our executives and managers.
You will learn the terms used by executives and managers in discussing Risk Management, and how to apply the concepts of Risk Management to your networks, systems, and projects. This course is not an operational or tactical course that focuses on how you will secure your networks, but instead focuses on the mindset of managers and teaches you how to think like they do. Once you master these concepts, it is much easier to build your business case for your projects and justify your budgetary needs.
Throughout this course, we will discuss what comprises Risk (assets, threats, and vulnerabilities), providing numerous real world examples along the way. We will also cover Qualitative and Quantitative Risk Measurements, showing how you can calculate the risk of an uncertainty due to vulnerabilities and threats.
This course also includes two case studies of what happens when risk management fails, as demonstrated by the Amazon Web Services outage and Equifax data breach that both occurred in 2017. You will learn to better understand these scenarios, what caused the outage/breach, and why managers may have made the decisions they did that led up to them.
Who this course is for:
Information Technology mangersCybersecurity managers
Aspiring managers
What you'll learn
Understand the foundations of Risk Management in the cybersecurity and information technology fieldBe able to use qualitative risk measurement techniques when discussing networks and projects
Be able to use quantitative risk measurement techniques when discussing networks and projects
Discuss current events in the technology space in relation to risk management decisions
Requirements
No special tools are required, just a willingness to learn about Risk Management in the Cybersecurity and Information Technology (IT) field
13. CompTIA Pentest+ (Ethical Hacking) Course & Practice Exam
Pass the CompTIA Pentest+ (PT0-001) exam on your 1st attempt, includes a Pentest+ practice exam!
Start now CompTIA Pentest+ (Ethical Hacking) Course & Practice ExamDescription
** Taught by a Best Selling Certification Instructor **This course provides everything you need in order to study for the CompTIA Pentest+ (PT0-001) exam, including a downloadable PDF study guide to follow along with as you progress through the videos and to review before test day!
Taught by an expert in information technology and cybersecurity with over 20 years of experience, this course is a fun way to learn what you need to know to pass the CompTIA Pentest+ (PT0-001) exam or to better prepare yourself to serve on your organization's cyber defense team or as an independent penetration tester.
The CompTIA Pentest+ (PT0-001) certification is an intermediate-level vendor-neutral certification that validates your knowledge and ability to plan/scope an assessment, understand the legal/compliance requirements, perform vulnerability scanning/penetration tests, and analyze/report on your findings. This certification was released on July 31, 2018 by CompTIA to fill a gap between the foundational-level CompTIA Security+ exam (for those with about 1 year in the field) and the advanced-level CompTIA Advanced Security Practitioner (for those with at least 5 years in the field). The CompTIA Pentest+ (PT0-001) exam is focused on the technical, hands-on details of the cybersecurity field, including how to emulate a cyber threat, infiltrate a secure network architecture, and conduct a penetration test against your organizational networks (with permission, of course).
This course is designed for penetration testers, IT Security analysts, vulnerability analysts and testers, network security operations personnel, or anyone who is trying to get a better understanding of the concepts involved in conducting a penetration test and its associated toolsets.
The CompTIA Pentest+ (PT0-001) exam covers FIVE domains:
15%: Planning and Scoping
22%: Information Gathering and Vulnerability Identification
30%: Attacks and Exploits
17%: Penetration Testing Tools
16%: Reporting and Communication
** Each video lecture comes with a downloadable PDF of all the lecture notes for your offline study needs **
What Other Students Are Saying About My Pentest+ (Ethical Hacking) Course here on Udemy:
I've taken several of Jason's courses and they all have been outstanding. This one is no exception. He provides a clear and concise review of each of the areas covered by the Pentest+ exam. If you have the requisite experience, this course will provide a great refresher for key points as you prepare to sit for the examination. (Steven, 5 stars)
I chose this course because i have recently finished the security+ course and really love the style of the instructor. I have no doubt this course will help and be a great addition to my comptia pentest+ study guide and hands on testing. (Rachel, 5 stars)
Jason Dion is both well-versed in the material as well as a solid teacher. I also took his CySA+ course last year and found it to be excellent. This PenTest+ course is more of the same quality content! (Chris, 5 stars)
Really enjoying this course. This is by far the best course to date. (Simon, 5 stars)
Who this course is for:
Students preparing for the CompTIA Pentest+ (PT0-001) Certification ExamSecurity Analysts
Penetration Testers
Vulnerability Testers
Network Security Operations
Application Security Vulnerability Testers
What you'll learn
Take and pass the CompTIA Pentest+ (PT0-001) certification examUnderstand the penetration testing methodology
Understand how to plan and scope a penetration test
Understand how to conduct information gathering and enumeration
Understand how to exploit networks and systems during a pentest
Understand how to prepare a report and communicate your findings
Requirements
Basic understanding of network and network securityUnderstand the concepts covered by the Network+ and Security+ exams
14. Marketing and Growing Your Udemy Course (Unofficial)
Strategies to market your Udemy courses without an existing audience & convert students into raving fans! (Unofficial)
Start now Marketing and Growing Your Udemy Course (Unofficial)Description
Are you new on Udemy and wonder why your brand-new course is not getting the sales it deserves?Or, are you a seasoned Udemy instructor looking to turn your students into raving fans who join your new courses within hours of their release? If so, this is the course for you!
In this course, you will get tips and tricks for how to market your new courses for a more successful launch, including the strategies to use on YouTube and Facebook to grow your brand and reach more potential students. You will also learn how to leverage other peoples's existing audiences by connecting with influencers to get your courses shown to large amounts of potential new students when you are just starting out.
You won’t just learn someone’s thoughts or theories on how to sell your Udemy course, you will learn what has been proven to work time and time again. We will give you the strategies that we use every single day to increase our brands and gain more students.
With over 200,000 students between our combined 52 courses, Diego Davila and Jason Dion are both considered top Udemy instructors...and we both started without an existing audience, just like you.
Udemy brought Diego and Jason together to present this course live at the 2018 Udemy LIVE! Conference in San Francisco, and now it is your chance to join this extended version of the course.
Are you ready to learn the steps needed to really see growth in your Udemy courses? If so, join us today!
Who this course is for:
Beginning Udemy instructors who want to expand their brand, grow their sales, and build their audiencesUdemy instructors
Online educators
Anyone who wants to learn how to build their audience
Anyone looking for free ways to do gorilla marketing...without spending ad dollars
What you'll learn
Utilize YouTube to gain studentsLeverage the audiences from other influencers
Build and grow a Facebook Group for your Udemy students
Convert your students into raving fans
Requirements
Students should know how to use YouTube, Facebook, and how to create a course on Udemy15. Introduction to Cloud Security with Microsoft Azure
Increase your cyber security capability by learning the fundamentals of cloud security inside of Microsoft Azure!
Start now Introduction to Cloud Security with Microsoft AzureDescription
Every organization is migrating to the cloud in order to save money, but is it really safe?Do you want to learn about "the cloud", how to secure it, and even how to build your own virtualized networks inside of the Microsoft Azure cloud computing platform? If so, this is the course for you.
In this course, you will learn the fundamentals of cloud-based service technologies, as well as how to best secure them. This course is designed for anyone who is new to cloud computing that needs to understand the basics of security and how they are implemented inside a cloud computing platform.
You won't learn just the theory, though. Throughout this course, we will provide you with an opportunity to apply your knowledge in the real world by creating your own virtualized network inside of the Microsoft Azure cloud computing platform.
By the end of the course, you will understand the difference between on-premise and hosted solutions, as well as SaaS, PaaS, and IaaS. We will cover single-tenancy and multi-tenancy solutions, as well as their security concerns.
So, if you have ever wanted to learn the basics of cloud computing, set up your own cloud architecture, or learn how to better secure your own cloud systems, this is the course for you!
What Other Students Are Saying About My Cloud Security Course here on Udemy:
Really untied all locks of AZURE. Amazing course.. Looking ahead more on Implementation of Azure training courses. (Manu, 5 stars)
This is a great course for someone who does not know anything about Microsoft Azure. It helps with the basics and helps you to get started in just a couple of hours. (Michael, 5 stars)
Great Intro to Azure Cloud Security. (Anthony, 5 stars)
Who this course is for:
Information Technology managersSystem administrators
Cybersecurity analysts
Aspiring manager and IT leaders
Future cloud architects
What you'll learn
Understand the difference between on-premise and hosted solutionsUnderstand the differences between SaaS, PaaS, and IaaS
Understand cloud computings vulnerabilities
Implement and secure your own environment within Microsoft Azure
Requirements
No special tools are required (you will get access to everything you need in this course)A Microsoft Azure account (if you wish to create your own cloud network as shown in the course)
16. CompTIA Security+ (SY0-501) Complete Course & Practice Exam
CompTIA Security+ (SY0-501) Bootcamp - Your preparation course for the most popular cyber security certification!
Start now CompTIA Security+ (SY0-501) Complete Course & Practice ExamDescription
**You can pass the CompTIA Security+ (SY0-501) Exam **
Taught by an expert in information technology and cyber security with over 20 years of experience, this course is a fun way to master the fundamentals of computer security.
My name is Jason Dion, and I have personally helped over 60,000 students earn their IT certifications, and now I can help you, too!
This course is designed to help prepare you for the CompTIA Security+ (SY0-501) certification exam and covers the six domains for the Security+ (SY0-501) certification exam:
Threats, Attacks, and Vulnerabilities
Technologies and Tools
Architecture and Design
Identity and Access Management
Risk Management
Cryptography and PKI
You will learn the fundamentals of cyber security and gain experience in the configuration, management, and troubleshooting of common wired and wireless networks.
What You Will Receive In The Course:
Video lectures with the essential information needed to pass the Security+ (SY0-501) exam
Downloadable copies of our Study Notes based on the lessons
Practice questions to ensure mastery of each section of the course
A full-length practice exam with multiple choice and mock simulations
What Other Students Are Saying About My CompTIA Security+ (SY0-501) Course:
I passed the Security+ exam. This course was absolutely essential to passing that exam. Only the Dion Security+ covered the topics comprehensively and thoroughly enough. No other resource I used came close. (Kolya, 5 stars)
I have just completed watching two different instructor corses on the same subject. I must say, Dion's has more information in a better constructed manner. This course is not easy, it is heavy with information and having you sit through shorter videos was the best part. Having watched more than just Dion's, I can say he goes over the content much better. Very glad I chose to watch a second course! (Rutger, 5 stars)
I love taking this wonderful course. It's full of important tips and amazing steps in order to pass CompTIA Security+. Thank you, Jason Dion, for making this incredible course! (Paul, 5 stars)
Who this course is for:
Students wanting to pass the CompTIA Security+ certification examStudents wanting to learn the terminology and nomenclature of computer security
Students seeking a career in cyber security
What you'll learn
Passing the CompTIA Security+ certification exam with confidenceUnderstand computer security, its functions, and its components
Performing basic security configurations
Become an effective security technician in a business environment
Requirements
Basic familiarity with computer networks, administration, and security is helpful (But, all required information will be covered during the course)(Helpful, but not required) Completion of the CompTIA A+ and Network+ certifications
17. CompTIA Security+ (SY0-501) Practice Exams with Simulations
Full-length CompTIA Security+ (SY0-501) Practice Exams * PBQs * Timed * 420 Questions with feedback!
Start now CompTIA Security+ (SY0-501) Practice Exams with SimulationsDescription
All questions are based on the Exam Objectives for the SY0-501 exam for all 6 domains of the exam, so you can take and pass the actual CompTIA Security+ (SY0-501) certification exam with confidence!In this course, I fully prepare you for what it is like to take the CompTIA Security+ (SY0-501) certification exam. These 6 full-length practice exams with 70 questions (including simulations or PBQs as CompTIA calls them) is timed for 90 minutes just like the real exam is. I have carefully hand-crafted each question to put you to the test and prepare you to pass the certification exam with confidence.
You won't be hoping you are ready, you will know you are ready to sit for and pass the exam. After practicing these tests and scoring an 80% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-schedule fees, saving you time and money.
You will receive your total final score, along with feedback on each and every question, telling you exactly why each answer is correct, and which domain you need to study more in order to pinpoint the areas in which you need to improve and perform some additional study.
Our CompTIA Security+ (SY0-501) practice exams provide you with realistic test questions and provide you with interactive, question-level feedback.
I have some of the highest-rated CompTIA training courses on the Udemy platform and I invite you to visit my instructor profile to learn more about me, the certifications that I hold, and read the reviews of my courses. This course is consistently updated to ensure it stays current and up-to-date with the latest release of the CompTIA Security+ exam, and also provide a 30-day money-back guarantee, no questions asked!
What others are saying about my CompTIA Security+ (SY0-501): Practice Exams with Simulations course:
The questions were tough and it took me about 3 times for each test to reach 100%. I hope they are like the test... Really hope. Great training resource because the explanations are very useful. (Rick, 5 stars)
Great tests that provide something close to the scenario based questions that the Security+ will show (it's hard as Udemy's platform isn't designed to allow them properly) Diverse questions. Really good explanations. Great learning tool for passing the test as the exams cover a lot off! (Aimee, 5 stars)
This course of practice exams has some good concept reinforcing questions, and does a good job of rotating/varying the types of questions asked. Highly recommend if preparing for SY0-501. (Matthew, 5 stars)
These questions are unique and well conducted to prepare for security+ with relevant information. I am using multiple resources and this is definitely one to have. (Valdrin, 5 stars)
Who this course is for:
Students preparing for the CompTIA Security+ (SY0-501) certification examRequirements
Basic understanding of networks and securityHave read a book, watched a video series, or otherwise started studying for the Security+ exam
18. ITIL 4 Foundation Practice Certification Exams (6 Exams)
6 Full-length ITIL 4 Foundation Timed Tests *** 40 Questions Each & 240 Questions Total (With feedback on each question)
Start now ITIL 4 Foundation Practice Certification Exams (6 Exams)Description
Have you already taken an ITIL® 4 Foundation course from a registered Accredited Training Organization (ATO)?Have you self-studied using the ITIL® 4 Foundation textbook?
Are you still not quite confident that you are ready to take the certification exam? If so, you've come to the right place!
I have personally trained over 20,000 people in how to pass their ITIL Foundation exams on the first attempt!
With my 6 practice exams containing 40 questions each, I have carefully hand-crafted each question to put you to the test. After passing these exams, you will be fully prepared for what it is like to take the ITIL 4 Foundation Certification Exam.
This practice exam course is designed around the official exam guide for ITIL 4 Foundation from Axelos, weighting the 12 Knowledge Areas properly, so you can pass the actual ITIL 4 Foundation Certification Exam with confidence!
You won't be hoping you are ready, you will know you are ready to pass the exam, saving you time and money. After practicing these tests and scoring an 80% or higher on them, you will be ready to PASS your certification on the first attempt and avoid costly re-scheduling fees.
After each practice exam attempt, you will receive your total final score, along with feedback on each and every question -- telling you exactly why each answer is correct so that you can pinpoint the areas in which you need to improve and perform some additional studying.
These ITIL 4 Foundation Practice Exams have the timed test taking capability and provides you with interactive, question-level feedback.
These practice exams are constantly updated to ensure it stays current and up-to-date with the latest release of the ITIL 4 Foundation exams, and also provides you with a 30-day money-back guarantee, no questions asked!
What Other Students Are Saying About Our ITIL 4 Foundation: Practice Certification Exams:
Very effective tool for preparing to take the ITIL Foundation exam! (Evon, 5 stars)
Thank you for the practice exams! Passed on the first try. Thanks again!!!!!! (Desmond, 5 stars)
These exams give the student a very good idea about how difficult the real exam questions will be. I was prepared, and passed the ITIL Foundation Exam this morning. Well worth the cost. (Steve, 5 stars)
** Dion Training Solutions (diontraining) is an Accredited Training Organization (ATO) for ITIL® 4 Foundation certification. These practice exams make an excellent supplement to your other study efforts for the ITIL® 4 Foundation certification, but should not be your only resource for studying for this exam. It is recommended that you attend a full training course prior to taking the exam. **
The ITIL® course on this page are offered by Dion Training Solutions, LLC, an ATO of AXELOS Limited. ITIL, ITIL Foundation, and the Swirl logo are registered trademarks of AXELOS Limited. All rights reserved.
Who this course is for:
Students preparing for the ITIL 4 Foundation certification examIT Service management professionals looking to validate their skills by passing the ITIL 4 Foundation certification
Requirements
Basic understanding of IT Service Management and/or how a service desk works
ITIL 4 Foundation training (Video-based course or textbook) from an Accredited Training Organization
19. PMP ®: The Complete PMP Course & Practice Exams PMBOK 6 2020
The complete PMP course - 35 contact hours/PDUs, 17+ hours video, 250+ questions, 40+ PM downloads, and 35+ assignments
Start now PMP ®: The Complete PMP Course & Practice Exams PMBOK 6 2020Description
You can pass your PMP ® Exam; We can helpGet your PMP ® training from a PMI ® Registered Education Provider (R.E.P.) - Thor Teaches LLC (REP #4906)
Taught by 4 expert Project Managers with 80+ years of combined Project Management work experience and 35+ years of teaching Project Management.
This training is based on the current PMBOK version 6 and PMP ® exam and includes all the new curriculum updates for the July 1st 2020 PMP exam changes.
We will give you the knowledge, tools, techniques, and approaches to pass your PMP certification and become a better Project Manager.
Included in this course:
Video lectures covering the entire PMP curriculum (17+ hours)
Combined PMP lecture notes from all the lecture slides (80+ pages)
35 Contact hours / PDUs *You HAVE to complete all lectures, quizzes, tests, and assignments to get the certificate of completion*
35+ Project Management templates for download.
10 domain specific practice questions for each of the PMP knowledge areas (60 total)
PMP study planner
A full 200 question PMP practice exam
Web links for all the PMP domains, general Project Management, PMI, and the PMP certification in general
Your instructors:
Jason Dion
150,000+ Students Worldwide - Best Selling Udemy instructor - CISSP, CEH, Pentest+, CySA+, Sec+, Net+, A+, PRINCE2, ITIL
Ku'uipo Laumatia Murray
20+ years of training PMP students, former college adjunct professor (Project Management), former PMI President of the Honolulu chapter, MBA, and Doctoral candidate in Education leadership.
Christine Rose
18 years of experience managing projects, programs, and portfolios. Master of Science in Project Management (MPM - Master Project Manager), and experienced educator and trainer.
Thor Pedersen
30,000+ Students Worldwide - Best Selling Udemy instructor - CISSP, PMP, CISM, CEH, CCNP, Security+, CCNA, CCNA-Sec
Our course is designed to help prepare you for the PMP Exam:
Introduction to the PMP certification and your instructors.
The Project Management Framework.
The Project Management Process Groups.
Initiating.
Planning
Executing.
Monitoring and Controlling.
Closing.
Agile Project Management and the Agile Practice Guide.
Applying the Project Management Process to your Project using the Gameboard approach.
PMP Exam preparation, PMP study plans, the PMP application, how to study efficiently and effectively.
** To get the 35 contact hours, you HAVE to complete all lectures, quizzes, tests and assignments to get the certificate of completion. **
Who this course is for:
Project Managers who are wanting to pass their PMP exam.
Project Managers who need the 35 contact hours to qualify for the PMP exam from a PMI Registered Education Provider (all included in the course).
Project Managers who want to earn 35 PDUs from a PMI Registered Education Provider (all included in the course).
Project Managers who want to learn Project Management from PMIs (Project Management Institute) perspective.
This is NOT for inexperienced Project Managers, for those we recommend CAPM classes.
What you'll learn
Prepare for the updated 2019/20 PMP (Project Management Professional) exam (next PMBOK update is scheduled for 2021).Clear understanding of the 5 Process Groups, the 10 PMP Knowledge Areas, and the 49 Processes.
Earn the 35 Contact hours needed for your PMP application.
Get all the resources you need to pass your PMP certification exam.
Understand Project Management from PMI's perspective.
Learn why you want to get your PMP certification and what it can give you.
Training by a PMI Registered Education Provider.
Earn 35 PDUs if you are already PMP certified,
Requirements
You should WANT to pass your PMP exam.Understand basic project management.
You should qualify for the PMP exam.
20. CompTIA A+ (220-1001) Test Prep, Exams and Simulations
Pass the CompTIA A+ (220-1001) Core 1 exam with help from an expert in the field!
Start now CompTIA A+ (220-1001) Test Prep, Exams and SimulationsDescription
The Computing Technology Industry Association (CompTIA), is a non-profit trade association, issuing professional certifications for the information technology (IT) industry. It is considered as one of the IT industry's top trade associations.[2] Based in Downers Grove, Illinois, CompTIA issues vendor-neutral professional certifications in over 120 countries. The organization releases over 50 industry studies annually to track industry trends and changes. Over 2.2 million people have earned CompTIA certifications since the association was established.[1]History
CompTIA was created in 1982 as the Association of Better Computer Dealers (ABCD).[3] ABCD later changed its name to the Computing Technology Industry Association.[4]
In 2010, CompTIA moved into its world headquarters in Downers Grove, Illinois. The building was designed to meet LEED CI Certification standards.[5]
The CompTIA portal moved to a hybrid version of the open-access model in April 2014 with exclusive content for due-paying members.[6][7] The move expanded the organization's reach to engage a broader, more diverse set of members and within a year, CompTIA's membership grew from 2,050 members to more than 50,000 in 2015.[8] By the close of 2016, the organization boasted more than 100,000 members worldwide.
CompTIA launched the Dream IT program in 2014 to provide resources for girls and women in the United States interested in the IT industry. In October 2015, the program was expanded into the UK.[9]
Skillsboost, CompTIA's online resource for schools, was launched in June 2015. It contained resources for students, parents and teachers to promote the importance of computer skills.[10][11] CompTIA held its first annual ChannelCon Vendor Summit in 2015. The Vendor Summit is exclusive to people attending ChannelCon, the industry's premier conference for collaboration, education and networking. It addresses issues within the IT industry.[12]
In January 2017, CompTIA launched an IT professional association built on its acquisition of the Association of Information Technology Professionals
All questions are based on the Exam Objectives for the 220-1001 exam for all 5 domains of the exam, so you can take the actual CompTIA A+ (220-1001) Core 1 exam with confidence, and PASS it!
In this course, you will get fully prepared for what it is like to take the CompTIA A+ (220-1001) Core 1 exam. This course doesn't just provide you with full-length practice exams (each of which is timed at 90 minutes), but it will also train you how to become a better test taker.
For most CompTIA A+ (220-1001) test takers, this is their FIRST certification exam in the Information Technology (IT) industry. If this is true for you, then you need this course to learn how to take these exams the proper way.
Certification exams are expensive to take, so you only want to take it one time and you want to pass it. This course is designed to help you do just that.
First, you are going to learn how the exam is developed and what to expect on the exam in terms of the number of questions, the length of the exam, the testing process, and other such fundamentals.
Then, you are going to learn how to perform better on the exam by using my Top 5 test taking techniques that have helped over 100,000 students (just like you) earn their industry certifications.
After that, you will put my tips into practice in two CompTIA A+ Core 1 (220-1001) full-length practice exams with 90 questions each. You will receive your total final score, along with feedback on each and every question, telling you exactly why each answer is correct, so you can pinpoint the areas in which you need to improve and perform some additional study.
These CompTIA A+ (220-1001) Core 1 Practice Exams will provide you with realistic test questions and provide you with interactive, question-level feedback.
After that, you will focus on the Performance Based Simulations (PBQs) for the CompTIA A+ (220-1001) Core 1 exam. Here you will learn all about motherboards, wireless configurations, mobile device configurations, command line troubleshooting with IPCONFIG and PING, and how to configure RAIDs. Each of these simulations are designed to ensure you will PASS the CompTIA A+ (220-1001) Core 1 exam come test day.
These PBQs (often called simulations by students) are the hardest questions on the exam, and this course will ensure you are ready to conquer them on the exam!
So, you won't be hoping you are ready, after this course you will know that you are ready to take and pass the exam. After practicing these tests and scoring an 85% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-schedule fees, saving you time and money.
I have some of the best-selling CompTIA training courses on the Udemy platform and I invite you to visit my instructor profile to learn more about me, the certifications that I hold, and read the reviews of my courses. This course is constantly updated to ensure it stays current and up-to-date with the latest release of the CompTIA A+ (220-1001) Core 1 exam to ensure your success. This course also comes with a 30-day, no questions asked, money-back guarantee, so you have nothing to lose by enrolling today.
What others are saying about my CompTIA courses:
This set of questions focused me on the required learning and was instrumental in my passing...well worth the cost... (Pranav, 5 stars)
Setup of the questions feels so like being in a real exam environment... loved it! (Behaviour, 5 stars)
This course really helped me to prepare and pass the PBQs on the 1001 exam. Hoping the 1002 edition is released before taking part 2 of the exam! Thank you! (Cory, 5 stars)
Who this course is for:
Anyone looking to take and pass the CompTIA A+ (220-1001) certification exam
Anyone who wants to understand how the PQBs and simulations are given on the exam
Anyone who needs to become a better test taker before attempting the CompTIA A+ (220-1001) certification exam
What you'll learn
How to pass the CompTIA A+ (220-1001) Core 1 exam on your first attemptHow to become a better certification exam test taker
How to answer the Performance Based Questions (PBQs) and simulation style questions
What your weak areas are in the CompTIA A+ curriculum so you can restudy those areas
Requirements
CompTIA recommends having 9-12 months of on-the-job experience before taking the CompTIA A+ (220-1001) exam (Recommended but not required)Have read a book, watched a video series, or otherwise started studying for the CompTIA A+ (220-1001) exam
Working knowledge of computers and small networks
21. LPI Linux Essentials (010-160) Complete Course and Exams
LPI Linux Essentials (010-160) Bootcamp - Your guide to earning your LPI Linux Essentials (010-160) certification exam!
Start now LPI Linux Essentials (010-160) Complete Course and ExamsDescription
**You can pass the LPI Linux Essentials (010-160) Certification Exam **Taught by an expert in information technology and cyber security with over 20 years of experience, this course is a fun way to master the fundamentals of Linux system usage and administration.
My name is Jason Dion, and I have personally helped over 120,000 students earn their IT certifications, and now I can help you, too!
This course is designed to help prepare you for the LPI Linux Essentials (010-160) certification exam and covers the five domains for the LPI Linux Essentials (010-160) certification exam:
The Linux Community and a Career in Open Source
Finding Your Way on a Linux System
The Power of the Command Line
The Linux Operating System
Security and File Permissions
You will learn the fundamentals of the Linux operating system, be introduced to numerous Linux distributions, and gain experience in the configuration, management, and usage of common open source software applications and the operating system.
In addition to learning the theory, you will also get step-by-step demonstrations in our practical labs to practice the theory and really learn how to use and configure Linux. By the end of the course, you will be comfortable within the command line and start to feel like a Linux professional!
What You Will Receive In The Course:
Video lectures with the essential information needed to pass the LPI Linux Essentials (010-160) examDownloadable copies of our Study Notes based on the lessons
Practice questions to ensure mastery of each section of the course
Two full-length practice certification exams with multiple choice questions
What Other Students Are Saying About My Certification Courses:
Great, precise, and to the point explanations of concepts. A big problem with books and even some other videos is that they can get too wordy for their own good. Jason gives great and short explanations. He also makes great use of real world ways of looking at things. (Emanuel R., 5 stars)
The course has great tempo and the instructor is upbeat and interesting. It is obvious he loves teaching the subject, I love learning from him. (Michael G., 5 stars).
The course was great, I took an entire week to watch the course and do the practice exams. Jason is great at explaining the concepts, and I'm happy to say that I am now certified! (Fernando D., 5 stars)
Once again I am impressed with this course from Jason. His teaching style is spot and his explanation of the course work perfect. Would recommend this course for anyone looking to get a start in Linux system administration, or wish just to learn the basics for personal knowledge. (Paul S., 5 stars)
Who this course is for:
Beginning IT professionals who want to expand into LinuxService desk analysts who want to become Linux adminsitrators
Cybersecurity analysts who need to better understand Linux
What you'll learn
Understand the Linux and open source industry and knowledge of the most popular open source ApplicationsUnderstand the major components of the Linux operating system
Gain the technical proficiency to work on the Linux command line
Gain a basic understanding of security and administration in Linux
Understand how to work with users, groups, and permission in Linux
Requirements
There are no prerequisites for this certification or courseA laptop or desktop to install Linux on during the course
22. LPI Linux Essentials 010-160 (6 Practice Exams)
Full-length LPI Linux Essentials Timed Tests ** 40 Questions Each & 240 Questions Total (With feedback on each question)
Start now LPI Linux Essentials 010-160 (6 Practice Exams)Description
** Dion Training Solutions is an Platinum Publishing Partner for the LPI Linux Essentials (010-160) certification **Do you need to earn your LPI Linux Essentials (010-160) certification? If so, you've come to the right place!
I have personally trained over 100,000 people just like you in how to pass their exams on the first attempt!
With 6 practice exams containing 40 questions each, I have carefully hand-crafted each question to put you to the test. After passing these exams, you will be fully prepared for what it is like to take the LPI Linux Essentials (010-160) Certification Exam.
This practice exam course is designed around the official exam objectives for the LPI Linux Essentials (010-160) certification, weighting the 19 Knowledge Areas properly, so you can pass the actual LPI Linux Essentials (010-160) Certification Exam with confidence!
You won't be hoping you are ready, you will know you are ready to pass the exam, saving you time and money. After practicing these tests and scoring an 80% or higher on them, you will be ready to PASS your certification on the first attempt and avoid costly re-scheduling fees.
After each practice exam attempt, you will receive your total final score, along with feedback on each and every question -- telling you exactly why each answer is correct so that you can pinpoint the areas in which you need to improve and perform some additional studying.
These LPI Linux Essentials (010-160) Practice Exams have the timed test taking capability and provides you with interactive, question-level feedback.
I have the best-selling LPI Linux Essentials (010-160) training courses on the Udemy platform and I invite you to visit my instructor profile to learn more about me, the certifications that I hold, and read the reviews of my courses. You won't be disappointed!
This course is constantly updated to ensure it stays current and up-to-date with the latest release of the LPI Linux Essentials (010-160) exams, and also provides you with a 30-day money-back guarantee, no questions asked!
What Other Students Are Saying About Our Practice Certification Exam courses:
Very effective tool for preparing to take the exam! (Evon, 5 stars)
Thank you for the practice exams! Passed on the first try. Thanks again!!!!!! (Desmond, 5 stars)
These exams give the student a very good idea about how difficult the real exam questions will be. I was prepared, and passed the exam this morning. Well worth the cost. (Steve, 5 stars)
Show employers that you have the foundational skills required for your next job or promotion.
Linux adoption continues to rise world-wide as individual users, government entities and industries ranging from automotive to space exploration embrace open source technologies. This expansion of open source in enterprise is redefining traditional Information and Communication Technology (ICT) job roles to require more Linux skills. Whether you’re starting your career in open source, or looking for advancement, independently verifying your skill set can help you stand out to hiring managers or your management team.
The LPI Linux Essentials (010-160) course on this page are offered by Dion Training Solutions, LLC, a platinum publishing partner of the Linux Professional Institute (LPI).
Who this course is for:
Students preparing for the LPI Linux Essentials (010-160) certification examIT professionals looking to validate their skills by passing the LPI Linux Essentials (010-160) certification
Requirements
Basic understanding of Linux and Linux administrationLPI Linux Essentials video-based course or textbook
23. CompTIA A+ (220-1002) Test Prep, Exams and Simulations
Pass the CompTIA A+ (220-1002) Core 2 exam with help from an expert in the field!
Start now CompTIA A+ (220-1002) Test Prep, Exams and SimulationsDescription
All questions are based on the Exam Objectives for the 220-1002 exam for all 4 domains of the exam, so you can take the actual CompTIA A+ (220-1002) Core 2 exam with confidence, and PASS it!In this course, you will get fully prepared for what it is like to take the CompTIA A+ (220-1002) Core 2 exam. This course doesn't just provide you with full-length practice exams (each of which is timed at 90 minutes), but it will also train you how to become a better test taker.
For most CompTIA A+ (220-1002) test takers, this is their FIRST certification exam in the Information Technology (IT) industry. If this is true for you, then you need this course to learn how to take these exams the proper way.
Certification exams are expensive to take, so you only want to take it one time and you want to pass it. This course is designed to help you do just that.
First, you are going to learn how the exam is developed and what to expect on the exam in terms of the number of questions, the length of the exam, the testing process, and other such fundamentals.
Then, you are going to learn how to perform better on the exam by using my Top 5 test taking techniques that have helped over 100,000 students (just like you) earn their industry certifications.
After that, you will put my tips into practice in two CompTIA A+ Core 2 (220-1002) full-length practice exams with 90 questions each. You will receive your total final score, along with feedback on each and every question, telling you exactly why each answer is correct, so you can pinpoint the areas in which you need to improve and perform some additional study.
These CompTIA A+ (220-1002) Core 2 Practice Exams will provide you with realistic test questions and provide you with interactive, question-level feedback.
After that, you will focus on the Performance Based Simulations (PBQs) for the CompTIA A+ (220-1002) Core 2 exam. Here you will learn all about various Windows tools (like Disk Management, Task Scheduler, MS Config, Network Connections, and the command line), how to remove malware, how to configure SOHO wireless networks, how to configure mobile device security, the Linux command line, and how to use a help desk/trouble ticket system. Each of these simulations are designed to ensure you will PASS the CompTIA A+ (220-1002) Core 2 exam come test day.
These PBQs (often called simulations by students) are the hardest questions on the exam, and this course will ensure you are ready to conquer them on the exam!
So, you won't be hoping you are ready, after this course you will know that you are ready to take and pass the exam. After practicing these tests and scoring an 85% or higher on them, you will be ready to PASS on the first attempt and avoid costly re-schedule fees, saving you time and money.
I have some of the best-selling CompTIA training courses on the Udemy platform and I invite you to visit my instructor profile to learn more about me, the certifications that I hold, and read the reviews of my courses. This course is constantly updated to ensure it stays current and up-to-date with the latest release of the CompTIA A+ (220-1002) Core 2 exam to ensure your success. This course also comes with a 30-day, no questions asked, money-back guarantee, so you have nothing to lose by enrolling today.
What others are saying about my CompTIA courses:
This set of questions focused me on the required learning and was instrumental in my passing...well worth the cost... (Pranav, 5 stars)
Setup of the questions feels so like being in a real exam environment... loved it! (Behaviour, 5 stars)
This course really helped me to prepare and pass the PBQs on the 1001 exam. Hoping the 1002 edition is released before taking part 2 of the exam! Thank you! (Cory, 5 stars)
Who this course is for:
Anyone looking to take and pass the CompTIA A+ (220-1002) Core 2 certification exam
Anyone who wants to understand how the PQBs and simulations are given on the exam
Anyone who needs to become a better test taker before attempting the CompTIA A+ (220-1002) Core 2 certification exam
What you'll learn
How to pass the CompTIA A+ (220-1002) Core 2 exam on your first attemptHow to become a better certification exam test taker
How to answer the Performance Based Questions (PBQs) and simulation style questions
What your weak areas are in the CompTIA A+ curriculum so you can restudy those areas
Requirements
CompTIA recommends having 9-12 months of on-the-job experience before taking the CompTIA A+ (220-1002) Core 2 exam (recommended but not required)Have read a book, watched a video series, or otherwise started studying for the CompTIA A+ (220-1002) Core 2 exam
Passed the CompTIA A+ (220-1001) Core 1 exam (recommended but not required)
24. Introduction to Service Management with ITIL® 4
Learn about service management, four dimensions, guiding principles, service value system, and the ITIL 4 practices
Start now Introduction to Service Management with ITIL® 4Description
The Information Technology Infrastructure Library (ITIL) framework has become the standard in IT Service Management across the globe. ITIL helps all organizations, regardless of their industry or business sector, provide their IT services using the most efficient and economical methods. The framework focuses on IT Service Management best practices and efficient operations, and is used in government, commercial, and non-profit organizations, alike.This course provides an introduction to service management and the new ITIL 4 Foundation certification exam, which is the entry-level certification in the ITIL framework and offers an exceptional overview of ITIL. By obtaining your ITIL 4 Foundation certification, you are showing employers that you understand the key elements, concepts, and terminology used in ITIL, including how operations move between each activity and process to create value in the service value system, and their overall contribution to the service management best practices.
Please note, this course is NOT a complete textbook replacement and DOES NOT cover the entire ITIL 4 Foundation exam objectives in-depth. This course is a free course to introduce you to the concepts of service management and the ITIL 4 framework in order for you to determine if studying for the ITIL 4 Foundation certification is right for you.
The free ITIL® 4 course on this page is offered by Dion Training Solutions, LLC, an ATO of AXELOS Limited. ITIL, ITIL Foundation, and the Swirl logo are registered trademarks of AXELOS Limited. All rights reserved.
Who this course is for:
Students who require a basic understanding of the ITIL frameworkStudents who want to understand how the ITIL framework can be used to enhance IT service management within their organizations
IT professionals or others working within an organization that utilized ITIL and who need understand the framework to contribute to an ongoing service improvement
Anyone who has an interest in the ITIL framework
What you'll learn
Describing the ITIL frameworkUnderstanding real-world examples
Applying ITIL 4 to your organization
Discuss ITIL 4 concepts with confidence
Requirements
No prerequisites (we will teach you everything you need to know)
A desire to learn

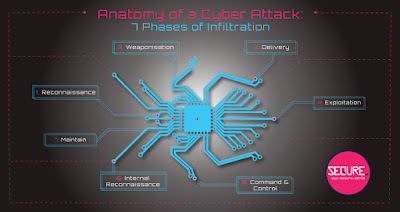









0 Comments:
Post a Comment